-
The Threat of SIM Swapping

A lot of online services and websites offer users the ability to protect their accounts using two-factor authentication through phone text. This post will go over a way that hackers have found in order to do just that. A SIM swapping is a technique used by a cyber-criminal in order to take control of accounts…
-
Cybersecurity Occupations

Happy Cybersecurity Month! Since it is Cybersecurity Month, it would be great to highlight career paths that can be present in Cybersecurity. Cybersecurity has become very prevalent and in demand since technology has become ubiquitous in our society. Cybersecurity is important because it helps to protect everyone’s information. Cybercrime Magazine gives a list of 50…
-
Keeping Data Safe

Happy Cyber Security Month! On Readwrite, Nirnay Butle, authors an article called “12 Things to Know About Cybersecurity Now.” In the article, it talks about ways people can lose their data which includes unauthorized links, spam messages, applications, weak privacy, and precaution. Here are some aways to keep your data safe: Internet links that have…
-
What is Malware?

Photo by Markus Spiske on Unsplash What is Malware? Malware, which is a combination of the words malicious and software, is an umbrella term for any kind of software designed with malicious intent. Not all malware is destructive, though it can cause annoying behaviors such as generating an abundance of pop-up ads or cause your computer to run slowly. In…
-
Data Breaches

Why should you care about data breaches and why are they a potential threat? A data breach is a security incident where information is accessed without authorization. Other terms for this are data spill, unintentional information disclosure, data leak, and information leakage. Data breaches can harm businesses and consumers in many ways. As technology progresses, more information is spread throughout the digital world, making…
-
What is the purpose of a firewall?
Even though we don’t think about it very often, network security is extremely important. This post is going to discuss a device that is used to enforce protection in networks. A firewall is a component that is used to monitor the incoming and outgoing traffic in a network. The term ‘firewall’ can be used to…
-
An Introduction to SQL Injection Attacks
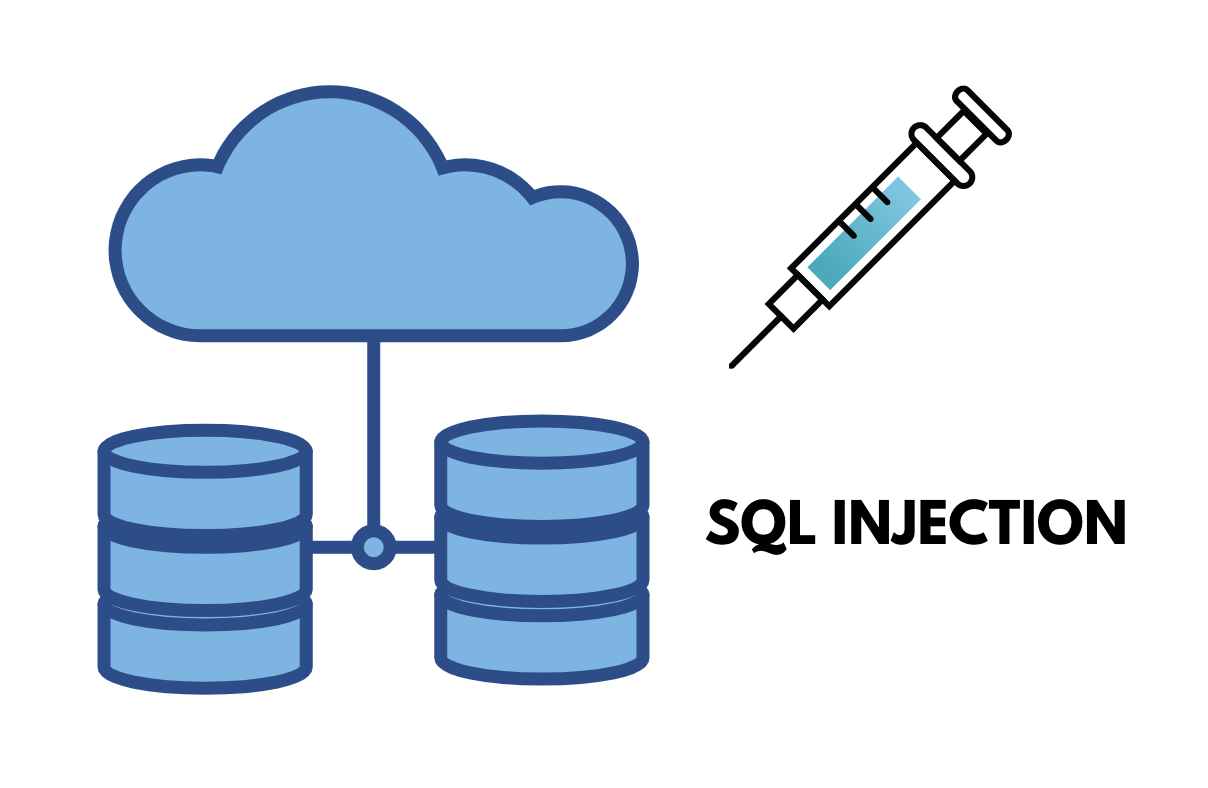
This Cybersecurity month, I wanted to introduce everyone to one kind of vulnerabilities that can exploited to take advantage of web applications. Many websites we use every day depend on databases for their backend infrastructure. Databases can be created and managed using a programming language called Structured Query Language (SQL). Statements written in SQL to…
-
Karen Hao

Karen Hao is an artificial intelligence reporter for MIT Technology Review. Hao’s focus is on the ethics and social impact of AI, as well as its applications for social good. She identifies herself as a tech reporter, experimental storyteller, and engineer. She is beyond what she claims herself. Hao dedicates her work to improving information…
-
Reshma Saujani

Reshma Saujani is an American lawyer and politician. She was born in Illinois and went to University of Illinois at Urbana-Champaign for majors in Political Science and Speech Communication. She attended John F. Kennedy School of Government at Harvard University for a Masters Degree in Public Policy and Yale Law School for a Juris Doctor…
-
Ann Mei Chang

former USAID Chief Innovation Officer Ann Mei Chang first began her career as a Senior Engineering Director at Google where she led the product development team for Emerging Markets. After 20 years in Silicon Valley, Chang moved her direction to the social and public sector as she served as Chief Innovation Officer at Mercy Corps…
